Cybersecurity
Protect your digital assets with our expertise in authentication, authorization, password management, and tailored security solutions. We prioritize your organization's security needs, offering robust protection against evolving cyber threats. Partner with us to build a resilient cybersecurity framework that safeguards your data and infrastructure effectively.
Execute Zero Trust security
Put Zero Trust into action with a modern, open approach to security that is aligned with your business priorities.
Authentication
TierSolution implements secure Authentication - the process of identifying users and validating are who they claim to be.
Authentication Methods We Implement:
- Password-based authentication – a simple and the common way most systems authenticate a user through username and password validation
- Passwordless authentication – verifying a user’s credentials through OTP or a magic link delivered to the registered email or phone number
- 2FA/MFA – requiring more than one security level, such as an additional PIN or security question to identify a user and grant access to a system
- Single sign-on (SSO) – managing users’ access to access multiple applications with a single set of credentials
- Social authentication – by verifying and authenticating users through existing credentials from social networking platforms (LinkedIn, OAuth, etc.)
- API Authentication – verifying users’ identities using either a session API key or security token
- Barcode Authentication – allowing users to be authenticated by scanning a barcode or a QR code
- Biometric Authentication - methods using distinctive biological features of individuals to validate identity

Authorization
Managing Authorization after a user’s identity has been successfully authenticated is about offering full or partial access rights to resources like database, funds, and other critical information.
Authorization Techniques We Provide
- Role-based access controls (RBAC) implemented for system-to-system and user-to-system privilege management
- JSON web token (JWT) open standard for securely transmitting data between parties where users are authorized using a public/private key pair
- SAML the standard Single Sign-On format (SSO) where authentication information is exchanged through XML documents that are digitally signed
- OpenID Authorization the authentication layer on top of the OAuth 2.0 framework used for authorization
- OAuth 2.0 Authorization the open-standard authorization protocol / framework that manages how unrelated servers and services can safely allow authenticated access to their assets without actually sharing the initial, related, single logon credential (also known as secure, third-party, user-agent, delegated authorization)
- Browser fingerprint Authorization method using an algorithm to generate a unique hash code based on the user's browser settings which is unique for each browser
With so many pros and cons to each method and technique, allow TierSolution to analyze your needs and help pick the best approach for you.
For example: the serverless token method is best method when scalability is an issue, or you are planning to scale. There is no caching to keep track of any requests on the server side but rather part of each request using the encrypted token. The session approach allows you to handle requests using a key that does not contain any sensitive information. If you need high performance to validate authorization, the session approach is also your best bet.

Password Management
Every company and its employees require tools to combat cyber threats and manage authentication processes. In order to meet system password requirements and to be able to create 1 unique password for every system, users need a tool to help them with these passwords challenges.
TierSolution built the most secure password management solution that exists on the market to help all users. Our approach to managing passwords is industry unique – our tools do not ask users to enter or reveal their passwords, therefore the password are not compromised. Users easily manage passwords using password hints instead, leaving the passwords out of the picture. Our solution eliminates the insider threats introduced by every other password management system on the market.
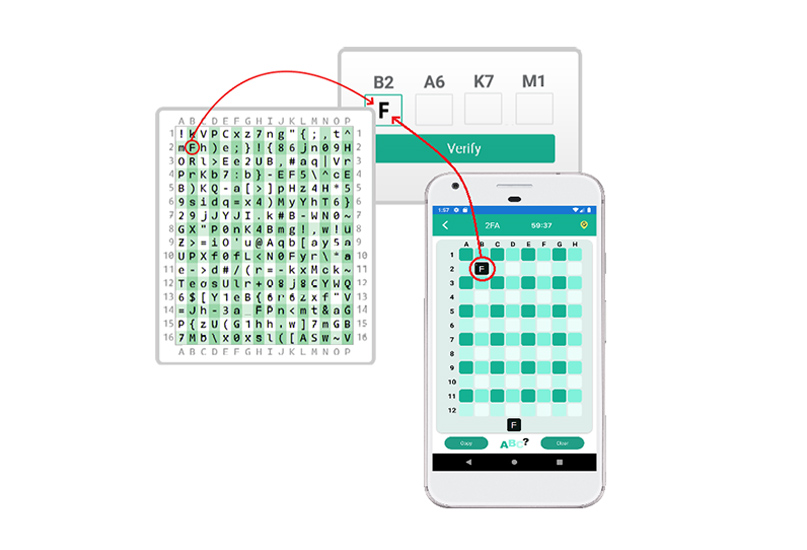
Multi-Factor
Authentication
TierSolution created one of the most secure MFA solutions on the market. The idea of adding extra layers during the authentication process is to reduce the risk of being compromised by phishing and middle man attacks, but most 2FA and MFA technologies fall short on protecting users against these type of attacks.
Our MFA solution reduces these risks and can be integrated into any existing system using our APIs and SDKs.